Furthermore, we outlined important steps to remove your email address from the Dark Web. We also provided a comprehensive guide on how to check if your email address is on the Dark Web. In this article, we discussed the significance of understanding the Dark Web and the reasons your email address may end up on it. By being aware of how your information is being used and taking swift action, you can significantly reduce the risk of your email address appearing on the Dark Web. By staying vigilant and proactive, you can minimize the risk of your email address being compromised and appearing on the Dark Web.
Hacking Groups And Services
And if you liked this article, follow us on LinkedIn, Twitter, Facebook, and YouTube for more cybersecurity news and topics. Great life advice, but it’s even more valuable where the darknet is concerned. That’s why it’s never a good idea to burn Tails on DVD. Just click on the onion icon and choose Security Settings. Tor has an in-build slider which lets you adjust the level of security.
Hoaxes And Unverified Content
The Dark Web Index is a powerful tool for accessing hidden services, but staying informed about risks is crucial. The Dark Web is a concealed portion of the internet, inaccessible via standard browsers or search engines like Google. It’s huge, making up about 90% of the internet, but it’s mostly mundane, hidden behind login screens for privacy and security. These pages come with extra protections for user anonymity and data security, and you need special software to access them—you can't get at them through your normal web browser, like you can with much of the rest of the deep web. However, no matter how much you try to stick to legal websites, you can still land on illegal or highly disturbing content. These sites are a hybrid tutorial-underground where wannabe hackers ask questions and professionals sell their services or stolen data.
What To Do If You Suspect Identity Theft
The Tor Project’s official onion site offers secure downloads of the Tor Browser and developer resources, helping users access and contribute safely to the Tor ecosystem. Many people seek it out for privacy and anonymity, as the Tor network and the Hidden Wiki help mask identities and activities from surveillance. We believe everyone should be able to explore the internet with privacy.We are the Tor Project, a 501(c)(3) US nonprofit.We advance human rights and defend your privacy online through free software and open networks. With Tor Browser, you are free to access sites your home network may have blocked. Onion sites are considered part of the deep web because search engines like Google and Bing can’t index them.
As such, we do not recommend using Tor if you want to do data-intensive activities like streaming in HD, gaming, torrenting, or making video calls. The anonymity provided by onion routing comes at the cost of slowing your internet considerably. Although it’s no longer active, it’s setting the standard for coming onion links.
Google’s business model depends heavily on tracking user behavior, collecting vast amounts of personal data to tailor ads and search results. One of the primary reasons users prefer the Hidden Wiki and similar dark web directories over Google is privacy. To appreciate why some users turn to the Hidden Wiki rather than Google, it’s important to understand the distinction between the surface web and the deep web. Enable security features in the Tor Browser, such as disabling JavaScript on unknown sites and avoiding plugins or extensions that may leak identifying information. Copy the .onion link carefully to avoid mistakes, as typos can lead to error pages or potentially malicious sites designed to impersonate the Hidden Wiki. This setup can help prevent network-level surveillance and reduce risks in environments where Tor use might be flagged or restricted.
Saved Searches
As a result, law enforcement has employed many other tactics in order to identify and arrest those engaging in illegal activity on the dark web. There have been arguments that the dark web promotes civil liberties, like "free speech, privacy, anonymity". The creator of Silk Road, Ross Ulbricht, was arrested by Homeland Security investigations (HSI) for his site and allegedly hiring a hitman to kill six people, although the charges were later dropped. The DWSN works a like a regular social networking site where members can have customizable pages, have friends, like posts, and blog in forums. Europol said several pedophile chat sites were also taken down in the German-led intelligence operation.
What Is The Hidden Wiki Used For?
Search the web for lists of .onion sites and you'll find some places to start. That's the whole point of a .onion address, after all. You're losing the anonymity you normally have when you connect to a .onion site through the Tor browser. After launching the Tor browser, type the .onion address into its address bar.

Instead, you need a specific configuration, software, or authorization, such as Tor, to access it. These sites aren’t just important resources; they’re like lifelines used to serve readers living under oppressive regimes. Everything you find on the dark web is not necessarily illegal. Not every visitor is a criminal, but this is where most cybercrimes begin. However, under the surface, they can provide total anonymity. It works by sending internet traffic through volunteer-operated nodes all over the world.
This adds another layer of protection when you’re visiting the dark web on top of the privacy and security our encryption and IP masking provide. ExpressVPN uses the best encryption on the market to protect your data. This just involves turning on your VPN before you open Tor and connect to dark web sites.
Browse Anonymously
From a legality perspective, individuals can navigate the dark web freely, but they should be aware of the potential risks involved. As the digital landscape evolves, understanding the legal and ethical considerations surrounding the adresse dark web becomes increasingly crucial. Proper research and careful browsing habits are crucial for anyone looking to explore this enigmatic space. One should always be wary when exploring this part of the web, as engaging with certain contents can lead to serious legal consequences. In conclusion, while the dark web offers unique opportunities and a sense of freedom, it carries significant risks.
Accessing The Dark Web

Pastebins are text sharing services, useful for sending and sharing large snippets of code or text. Once installed, the browser is simple to launch, and it automatically connects to the Tor network. Lastly, consider using a trusted security tool or firewall on your device and stay informed about the latest dark web threats through reliable sources.
Unblocked Browsers For Unrestricted Access In 2025

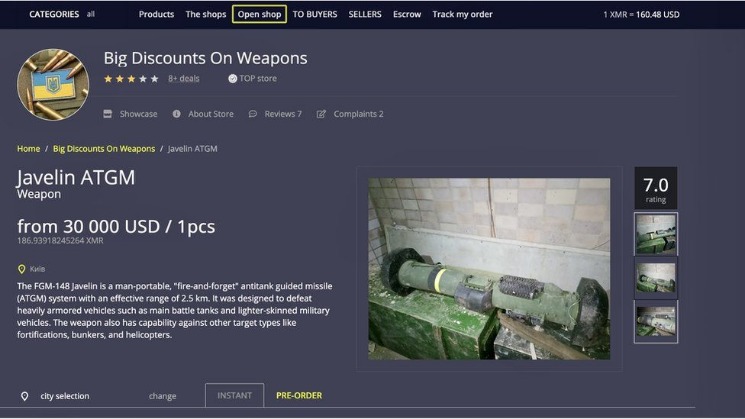
The dark web is infamous for containing sites such as Silk Road and other marketplaces where users could potentially buy drugs and/or weapons, stolen credit cards, IDs, and much more. Unlike the surface and deep web, you can’t access the dark web via a standard or specialized search engine. You can also find email messages, online bank statements, and much more information on the deep web – information that is usually private and inaccessible by the public on the surface web. The deep web is basically all the content that you can’t find using Google or Yahoo search. In addition, the content on the pages don’t need any special or custom configuration to access. The surface web (often referred to as the “visible web”) is the portion of the web available to the general public and indexed in the standard web search engines such as Google, Bing, and Yahoo.
It has a feature called CoinJoin that combines multiple coins from different users into a single transaction. Your data is encrypted in the Tor browser before reaching the ZeroBin servers. It is a reliable messaging tool where you copy/paste a text or image and send it to your addressee. ZeroBin is a wonderful way to share the content you get from dark web resources. Blockchain even has an HTTPS security certificate for even better protection.
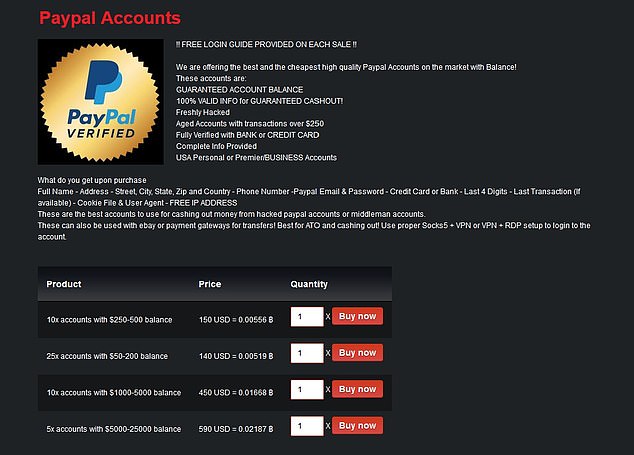
- This data can later be sold to identity thieves on the dark web.
- Sci-Hub gives access to millions of scientific papers, mostly ones from behind paywalls.
- One of the most popular ways to get around the dark web is not to use a search engine at all.
- For example, the BBC website is not accessible in such countries.
- Also known as deep web sites, these pages typically have URLs ending in .onion and are only accessible through special software like the Tor Browser.
You could be monitored closely even if you are not doing anything illegal. For example, the Silk Road site operator, an illegal dark web marketplace, was traced and arrested. Moreover, malicious actors can attempt phishing scams to steal your data and identity for extortion. Unfortunately, others are fake and fraudulent websites that exploit the reputation of the dark web to con people. Because of this, some people use it to get around government restrictions, while others use it for illegal activities like smuggling drugs and weapons. If you don’t take the necessary measures, many unsavory activities can expose you to unnecessary risks.
As I’ve mentioned, the dark web isn’t just a place of eternal torment, teeming with drug dealers, human traffickers, and a hitman. Sure, it’s not as secure as the clear web version, but it’s there and totally legal to use. In terms of functionality, I don’t think there are too many differences between regular IMAP, POP3, and SMT services and the stuff you can use to communicate on the dark web. So, it’s only natural to find ways to keep in touch with your darknet buddies and/or customers. Of course, you can’t use your home address for dark web drop-offs, but apparently, they can ship all over the world, minus some Middle Eastern countries and North Korea. By the way, most have shipping services.
As users seek to expand their knowledge or find community, always prioritize accès sécurisé practices to navigate this complex digital landscape effectively. While exploring the Dark Web, it is crucial to exercise caution and be aware of the varied types of content available. These communities often encourage sharing best practices to enhance online safety, further highlighting the constructive potential of the Dark Web.



