
Journalists, activists, and individuals concerned about online privacy and security often use it. Many countries, such as Qatar, China, Cuba, Russia, and Turkey, censor internet content promoting political dissent. People who live under a government that deeply supervises or censors internet traffic eventually get attracted to the dark web. However, it’s illegal if you venture into the dark web to commit unlawful actions such as downloading child porn, buying fake documents, drugs, credit cards, and more. The dark web’s anonymity makes it difficult for law enforcement to track down these criminal activities, leading to a rise in their prevalence. For Example, In May 2021, authorities in Germany brought down Boystown, a child pornography network with more than 400,000 registered users.

Anonymity & Privacy
To access the surface web or the deep web, all you need is a standard internet browser like Google Chrome or Safari. Once you’ve chosen a VPN provider and have successfully set up your account, you’re ready to start looking at overlay networks. VPN stands for virtual private network, and it acts as a security bubble for communications from your device. The first rule for accessing the dark web is to go into it with a purpose or a defined goal.
Find Legitimate Dark Web Links And Enter Them In Tor
In the summer of 2017, a team of cyber cops from three countries successfully shut down AlphaBay, the dark web’s largest source of contraband, sending shudders throughout the network. Even commerce sites that may have existed for a year or more can suddenly disappear if the owners decide to cash in and flee with the escrow money they’re holding on behalf of customers. For example, a popular commerce site called Dream Market goes by the unintelligible address of “eajwlvm3z2lcca76.onion.”
To reduce the risk of these threats, it’s highly recommended to disable JavaScript when browsing dark web sites. If you’re unsure about a link, do some research or ask trusted sources within dark web communities. Be cautious of random or obscure links — these could lead to dangerous or malicious websites. Unlike the clear web, where websites are often rated or reviewed, most dark web sites are unregulated. ExpressVPN is my top recommendation for Tor VPNs because it’s fast, easy to use, and its no-logs policy has been independently audited and confirmed by third-party cybersecurity experts.
How To Access onion Sites Safely
Proton VPN is part of the Proton family of services provided by Proton Technologies AG. Its VPN Accelerator distributes the CPU load between multiple processes in OpenVPN, and modifies the servers’ Linux stacks to shorten the normal packet processing path. Internet traffic is protected using 256-bit AES encryption, together with a SHA384 hash and 4096-bit RSA keys for OpenVPN and IKEv2. Tor Over VPN servers are identified with an onion symbol and found in the country list. Installing ExpressVPN on your router provides protection for all the devices on your home network.

The Best Dark Web Search Engines In 2024
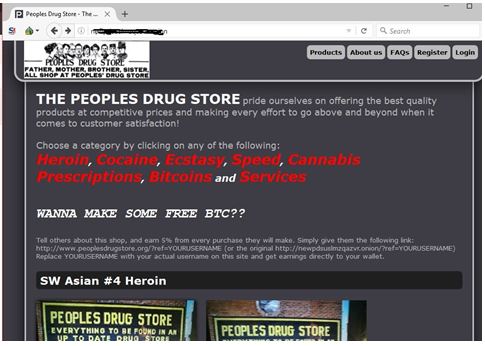
You should only ever access websites you know are safe because they're vetted by websites or other sources that you already know are safe. But be warned, it's not as user-friendly as the typical clearnet websites you access. It uses the onion router to bounce your signal around other Tor users around the world, thereby pseudo-anonymizing you when you access the dark web. There are many legitimate websites on the dark web that can be worth visiting, but there are also the absolute extremes of illegal material, such as pornography, illegal substances, and gore.
How To Access The Dark Web (Safely)
These laws mark how long ISPs must save the data they collect. With all this data, your ISP could create a very accurate profile of you and link it to your IP address. Tor Bridges or a VPN will help you to use Tor privately, as your ISP (Internet Service Provider) will not see that you’re connected to a Tor node. It is highly advisable to take all the necessary security measures discussed in this article to protect yourself. You can access the dark web using your Android device by following a few steps. Generally, it’s important to use Tor responsibly and in accordance with local laws and regulations.

Can Cybersecurity Teams Use The Dark Web To Track Threats?
Dark net websites are called “Tor hidden services“, and they can be distinguished from normal websites by their URLs. Even when using security measures and your common sense, accessing deep web content still poses a risk. Although websites can’t identify you and ISPs can’t decrypt your internet traffic, they can see that Tor is being used. The dark web is just a part of the internet that isn’t indexed by traditional search engines and requires special software like the Tor Browser to access. This is why it’s important to visit only well-known, reputable sites with a history of providing safe, reliable information or services. Additionally, while the Tor Browser (the most common tool for accessing the dark web) has some built-in privacy and security features, it’s not 100% safe..
- Staying cautious is essential when interacting with content on the dark web, as illegal activities are prevalent.
- When you install a VPN, all of your activities on the dark web will be hidden from unwanted snoops from your ISP or the FBI.
- While some threats on the dark web are well-known, others may use its notorious reputation to trick users into paying large sums of money.
- Accidentally downloading or viewing illegal materials may result in severe legal consequences.
- The indie game Sad Satan was claimed to have been found via the dark web, but inconsistencies in the reporting cast doubt on the story.
The dark web provides a framework for secure communication, especially in regions where online activity is monitored. These include the sale of drugs, weapons, counterfeit documents, stolen data, and illegal pornography. While it enables privacy for legitimate activities such as whistleblowing, political dissent, or private communications, it is also used for illegal operations. Some services deliberately change their .onion addresses periodically to avoid detection or takedown, adding an extra layer of obscurity. The most common tool is the Tor network, which uses onion routing. This includes databases, academic journals behind paywalls, webmail accounts, online banking, and intranet systems.
Additional Security Measures
Cybercrime is getting more sophisticated, putting businesses at a serious disadvantage when it comes to protecting their networks. However, if you’re going to venture into the dark web, you’ll need to be well–prepared, so keep reading to keep safe. The internet is almost unfathomably large, and most of us are only actively engaging with between 4-5% of it. Dive into the world of modern cybersecurity with explanations, predictions, and expert opinions

Good Password Ideas And Tips For Secure Accounts
Despite this, many people prefer not to advertise to their Internet Service Provider that they are accessing the dark web. Content in the dark web is designed to be hidden and you’ll need special software to access it. Anonymity doesn’t make carrying out illegal acts any more permissible, so be cautious about making purchases or downloading content. More seriously, free VPNs – particularly those offered as standalone services – sometimes make money by selling your data to third parties.
- Here's how to access the dark web safely and anonymously.
- This supports damage control efforts and helps prioritize which systems, users, or customers require urgent remediation.
- Tor users in the USA, in particular, may want to use a VPN, which will be faster and more reliable.
- Although the social application is known for collecting data on its platform, it does not like sharing the information with others.
Web crawlers run the regular internet, scouring the web to discover newly published websites or pages in a process called crawling. The dark web is a small subset of the deep web comprising purely non-indexed websites and services. It comprises websites that aren’t easily accessible mainly because they are non-indexed, password-protected or paywalled.
Sending Group Texts On Pixel 6: The Definitive Guide
That means that even if an ISP is monitoring all of the known Tor relays, they may not be able to block all of the obfuscated bridges. Unfortunately, some oppressive regimes have figured out a way to block Tor traffic. One of the major advantages of using Tor in overly-restrictive countries is that it keeps your online travels private. Check out my article for more information about the dark web and how to access it while staying safe. This is why I strongly advise anyone visiting the dark web to exercise the greatest of caution during their dark online travels.



